
Revolutionizing Online Data Security with SecureAF: A Comprehensive Review
CybersecurityDescription
Vibe coding made Provably secure
Website Preview
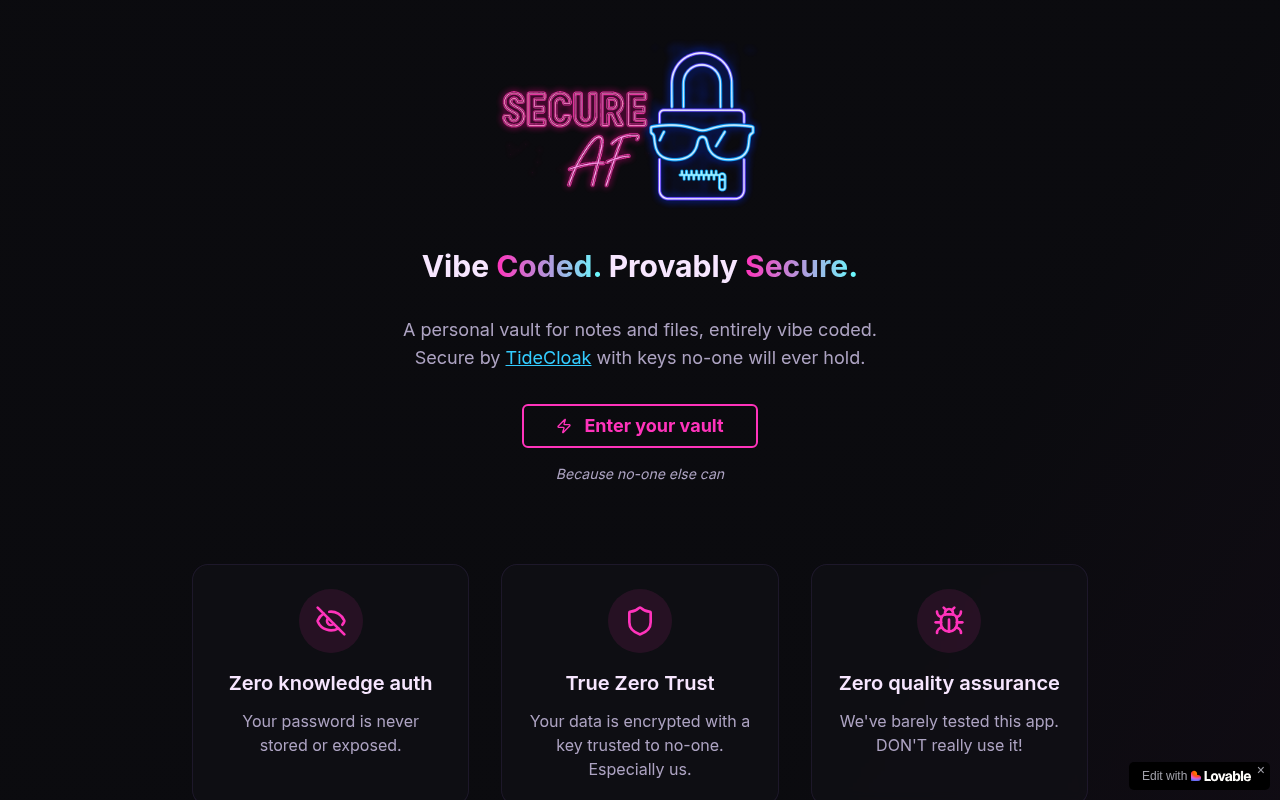
Click to view full size
About This Website
Introduction
In a world where cybersecurity concerns are a constant threat to the safety and privacy of our digital identities, there emerges a product aimed at securing the essentials. SecureAF positions itself as a unique solution in the cybersecurity niche, focusing primarily on aggressing everyday vulnerabilities and providing an impregnable shield for your data. Despite the company's self-deprecating acknowledgment of their less-than-perfect code quality and interface, they promise unrivaled security for users' personal information.
Overview of SecureAF
SecureAF proudly claims, "The code is rubbish. The UI questionable. QA nonexistent." This remarkably candid admission sets a tone that while peripheral features might be basic, they expend their best efforts where it matters most: securing users' data. This product uses advanced cryptographic keys as its primary defense mechanism, ensuring that your data, identity, and transactions are protected in a manner that neither hackers, vendors, nor even SecureAF itself can compromise.
Key Features and Encryption Standards
SecureAF utilizes cutting-edge cryptographic protocols to lock data securely. These keys are uniquely generated and are inaccessible to anyone, including the operators at SecureAF, creating a truly private and secured environment. This approach ensures:
- End-to-end encryption: Every piece of data, regardless of its nature, is encrypted from the moment it leaves the user.
- Zero-knowledge architecture: SecureAF does not have the ability to decrypt or access your data, ensuring complete user privacy.
Usability Despite Flaws
Despite straightforward admissions about its flaws concerning UI/UX implementation and the overall product finish, SecureAF focuses on what really matters—security. The user interface, although said to be "questionable," provides sufficient functionality without compromising on security. This decision to prioritize the encryption and security mechanisms over aesthetic aspects may appeal significantly to users who hold privacy above all else.
Why Choose SecureAF?
For anyone whose priority is uncompromised data security, SecureAF offers a robust solution. Its dedication to encryption and privacy makes it particularly appealing for:
- Users residing in or interacting with high-surveillance or high-risk environments.
- Businesses that need to safeguard sensitive client information against breaches.
- Technological implementers looking for an additional layer of security to shield data transactions.
Potential Beneficiaries and Use Cases
- Tech-Literate Individuals: They will appreciate SecureAF’s emphasis on robust encryption despite other product limitations.
- Small to Medium Enterprises (SMEs): SMEs looking for cost-effective yet strong security solutions can utilize SecureAF for protecting client data.
- Developers and Startups: Those involved in developing applications that require an added layer of security can integrate SecureAF’s technology into their projects.
Conclusion
In conclusion, SecureAF resonates with the needs of technology users and administrators who are serious about security, forgoing the frills of cutting-edge design for the essentials of data protection. While it may not win any prizes for user experience, its unyielding commitment to securing user data with top-notch cryptographic practices makes it a noteworthy product in the field of cybersecurity. This focused approach to security encapsulates their ultimate value proposition: maximum security in data handling, where it counts the most.
Featured Links
Foundation models that enable digital humans to see, understand, and move.

Comments (0)
Please log in to leave a comment.